|
Why buy GlowWorm FW? If your computer was hacked and used as a node on a botnet
to send spam, host illegal content or attack other computers, would you know? If you
knew, could you fix it? Home firewalls help prevent hackers from directly attacking
your computer. However, malicious web sites can be used to gain access to your computer
by exploiting security vulnerabilities in your web browser, email client and other
programs that you use to access the internet.
GlowWorm FW prevents applications from accessing the internet in ways that you
have not explicitly allowed. Your email client can be restricted to your
mail server. Your web browser can be restricted to the web sites that
you visit. Rules can assigned to a particular user so that you can apply more restrictive
settings for your children.
GlowWorm FW can prevent your computer from being useful to hackers while not being
cumbersome to you. As you use GlowWorm FW and customize it to fit your needs you will
find that it becomes less and less noticeable, while it continues to work in the background,
protecting the security of your Mac.
Network security for your Mac. Peace of mind for you.
[GlowWorm FW - Only $29.95]
GlowWorm FW builds on the Lite version by expanding the possibilities for Rule definitions,
adding flexible, per-rule logging, listener and incoming socket support and much more.
GlowWorm FW is now available for only $29.95! You can try out all of these features by obtaining
a free demo registration code (5 hour time limit, 30 day expiration) from the
download page. Be sure to choose the GlowWorm FW option
from the Product selection list.
Requires Mac OS X 10.4.
- Growl notification support in Rule Actions
- Control outgoing connections
- Control listener connections
- Control incoming connections
- Define up to 1,000 rules
- Limit the scope of a rule by specifying up to 10 TCP local or remote endpoints per rule
- Limit the scope of a rule by attaching up to 10 applications per rule
- Limit the scope of a rule by specifying up to 10 local users
- Limit the scope of a rule by specifying up to 10 local groups
- Define rules for an application which expire when that application quits
- Define rules which expire the next time your machine reboots
- Define rules based on relative network names, like localhost, localnet and remotenet - so that you don't have to "hard code" specific ip subnet addresses - very useful for mobile users
- Audio alert notification of network connection activity
- Kernel based rule evaluation for exceptional speed
- Plug-in architecture to support third party features
- System can automatically activate at boot time
- System supports pid-to-path for processes started before GlowWorm
- System tracks process names accurately during process fork()'s and exec()'s
- Authorization alert dialog with geocoding and reverse dns support
- Authorization alert dialog indicates the process owner shortname & real name
- Authorization alert dialog indicates the relevant ethernet interface
- Configurable auto-allow/deny for authorization alerts based on a timeout
- Drag-and-drop rule re-ordering
- Rule Editor shows match-count and last-match-date for each rule
- Rule Actions provide user-customizable alerts when a rule is matched
- Logging support on a per-rule basis
- Rule Editor supports viewing the last 100 log entries for each rule, or you can open the plain-text log files in your favorite text editor
- Application Monitor plugin show real-time information on application network activity
- Rule Editor & Application Monitor support window size and position state saving and restoring
- Rule Editor table supports column reordering, resizing, displaying extra columns (iTunes-style) and in-line editing of some values
- Magic [Black|White] Lists "magically" append criteria to existing rules based on your authorization decisions. See the full description below for more details.
- True DNS Names determines which host name a given connection should be associated with, without relying on reverse dns. See the full description below for more details
| [Rule Editor - Main] |
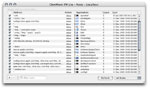 |
|
GlowWorm FW comes with the Rule Editor plugin, which provides an intuitive interface for
easily modifying the in-kernel network rules. Several frequently used parameters are viewable
and editable directly, while double-clicking on a rule will reveal a panel for modiying all
other aspects of the rule. Re-ordering rules is as simple and dragging-and-dropping.
|
|
| [Rule Editor - Options] |
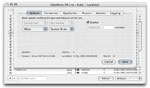 |
|
The Rule Editor Options tab displays basic information about the rule and allows one to
modify the basic parameters for the rule such as whether the rule is enabled or not, the
rule's categorization and what action to take when the rule is matched.
|
|
| [Rule Editor - Connections] |
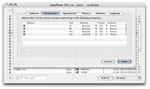 |
|
The Rule Editor Connections tab allows one to define the network specific parameters of the
rule. Each connection parameter can include a DNS host name, ip address or ip address range,
a port number or port range, a direction (incoming, outgoing, listener), a protocol (just
tcp for the time being), and an endpoint (local, remote). GlowWorm FW Lite is limited to five
connections per rule and does not support incoming/listener connections or local endpoints.
|
|
| [Rule Editor - Applications] |
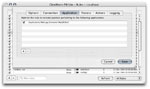 |
|
The Rule Editor Application tab allows one to define which application(s) this rule applies
to. Several applications can be specified for a single rule. GlowWorm FW Lite is limited to
a single application per rule.
|
|
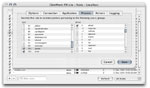
| [Rule Editor - Process] |
 |
|
The Rule Editor Process tab allows one to define the process specific parameters of the rule.
Using NetInfo, a list of local user accounts and groups is automatically obtained and displayed,
and with a simple click of a checkbox, a rule can be limited to a specific set of users and/or
groups. This feature is not available in GlowWorm FW Lite.
|
|
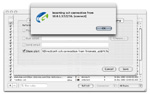
| [Rule Editor - Action] |
 |
|
Every rule can have actions associated with it that are performed when an event matches on
that rule (beyond simply allowing or denying a connection). The Alert action is the first
supported action. Using the alert text field, one can
create a custom alert message containing the pertinent information. The screenshot shows an
alert dialog which is displayed each time an outside user tries to ssh in to the local machine.
Rule actions are not available in GlowWorm FW Lite.
|
|
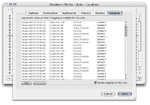
| [Rule Editor - Logging] |
 |
|
Essential to any security conscious user is logging. A simple click of a checkbox enables
logging on a per-rule basis. Log data is written in an easily-parsable plain-text format,
and the Rule Editor provides a simple interface for accessing the last 100 log entries.
Each log entry includes a timestamp, the local and remote endpoints, and the relevant action.
Logging is not available in GlowWorm FW Lite.
|
|
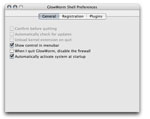
| [Rule Editor - Preferences] |
 |
|
GlowWorm.app provides a preferences window for configuring the general behavior of GlowWorm,
such as whether or not to display the menubar icon, and whether or not to automatically
activate the system when the machine starts up. Enabling GlowWorm at boot time maximizes the
effectiveness of the system by allowing it to run before most other processes (and specifically
processes that create listeners) start.
|
|
| [Menubar App - Alert] |
 |
|
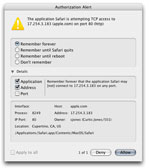
Menubar App provides the authorization interface that allows the kernel extension to solicit
feedback from the user in situations where the active rules do not conclude whether to allow
or deny a particular connection. The alert dialog shows all manner of information about the
process (unix user name, real name, user id, process id, application name) and the socket
connection (geocode lookup, ip address, port number, reverse dns lookup). Further, if you
want to create a rule to remember the decision that you make in this instance, several options
allow you to customize a basic rule to do just that. This new rule can even be limited in
scope to the lifetime of the particular application or simply until you reboot your machine.
One can also easily choose which aspects of the connection (application, address, port) to
include in the new rule.
|
|
| [Menubar App - Preferences - General] |
 |
|
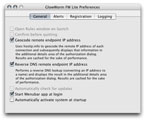
The preference pane for the Menubar App allows one to selectively enable or disable alert
geocoding and reverse dns. One can also choose to automatically active the system at startup,
and also automatically run the Menubar app when you log in.
|
|
| [Menubar App - Preferences - Alerts] |
 |
|
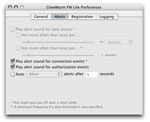
The alerts preference pane for the Menubar App allows you to customize the audible alerts.
With audible alerts enabled, a fairly non-annoying sound indicates when socket connections
are created, thus removing some of the need to monitor log files. Additionally, the
auto-answer feature allows you to specify the default action to take, and how long to wait,
if you do not answer the alert dialog.
|
|
| [Application Monitor] |
 |
|
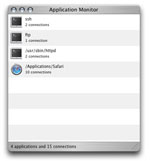
The Application Monitor is another plugin for GlowWorm. It displays information about
applications that are presently using network resources. Specifically, you can see how many
socket connections each application is using. If you ever wondered what application was
responsible for some network activity you just noticed, this can make it much easier to
identify.
|
|
| [Magic [Black|White] Lists] |
|
|
Magic Lists make running an outgoing-connection based software firewall more useful than it is
annoying. A security-conscious user would only permit one's web browser (Safari, FireFox, etc.)
to connect to the web sites that one visits. But that's a sizable hassle. Enter Magic Lists.
By setting up an Ask rule for your browser and enabling both magic white and black lists, each
time you make an authorization decision, the address information from that decision is appended
onto the appropriate white/black list rule so that you do not have to make that same decision
again. Without Magic Lists, one can have "Remember Forever..." always selected, but then one
will end up with an unmanageable number of rules.
The Magic black/white list rules appear just like every other rule, so you can view it and
remove previous decisions or add additional criteria.
More importantly, you do not end up falling prey to the concept of a "trusted application",
which is prevalent among other software firewalls. By trusting your web browser implicitly,
an attacker can use your browser for network access without your knowing.
|
|
| [True DNS Names] |
|
|
When your web browser contacts a web site, it first performs a DNS lookup to determine the Internet
Protocol address (IP address) of the web site. This process finds the address 216.109.112.135
when you try to go to yahoo.com, for instance. When your web browser has received this
IP address and attempts to contact the web site, the connection only has the IP address associated
with it, so the Authorization Alert dialog does not know what web site name you typed into the
web browser.
With True DNS Names, this is no longer the case.
|
|